Jim and Mike on Password Security and LastPass
Published May 26, 2023
Courses Mentioned in this Post: Data Privacy and Technology
Series Mentioned in this Post: Harvard On Digital
A Dashlane study conducted in 2017 says the average American Internet user has 150 online accounts that require a password. That’s a lot of passwords—or variations on similar passwords. According to Zippia, almost 200 million digital records have been exposed in the United States each year since 2015 and it is estimated that at least one out every three Americans are hacked each year. How can we maintain strong passwords to keep our information safe without having to reset them every time we log in to one of our 150 accounts?

Mike Smith and Jim Waldo
That's where password managers and other digital security technologies come into play.
LastPass is a popular password management tool that, until recently, was known for its convenience, efficiency, and enhanced security. However, in August 2022, a hacker breached the company’s customer database through an employee’s home computer and stole the account and password data of more than 30 million LastPass customers. This incident has called the safety and security of LastPass and similar services into question.
Experts in the field of computer science and data privacy, Michael D. Smith (Professor of Engineering and Applied Sciences) and Jim Waldo (Professor of the Practice of Computer Science), answer questions about this LastPass breach and offer their thoughts on ways you can protect your personal data and accounts.
Do you use LastPass to store your passwords?
Michael D. Smith (MDS): Yes, and I still do despite the recent breach. Centralization of secret information is convenient and a huge security risk. But given the proliferation of sites on which you have to create a login and password, you either use one of these password managers or use a couple of passwords across many sites. The former is still—assuming you use a very strong password for your manager—a better risk than the latter.
Jim Waldo (JW): I don’t use LastPass, but I do use a password manager. But I hope that we can move beyond passwords as a mechanism for authentication soon.
Passwords are, in many ways, the pessimal mechanism for authentication—they are hard for people to generate and remember, and easy for computers to guess. I tend to use pass phrases rather than pass words, often lines of songs or poems that I remember. These are easier to remember than a random collection of letters and numbers, and often more secure since they are longer. But we will be better off when using two-factor authentication (something you have as well as something you know) which allows enhanced security with weaker passwords.
What are some ways you protect your own data?
JW: There are some simple things that anyone can do to make their data more secure. Use two-factor authentication. Encrypt your disk (modern operating systems allow this in a painless way). Make sure that you only interact with websites that are running https: protocols.
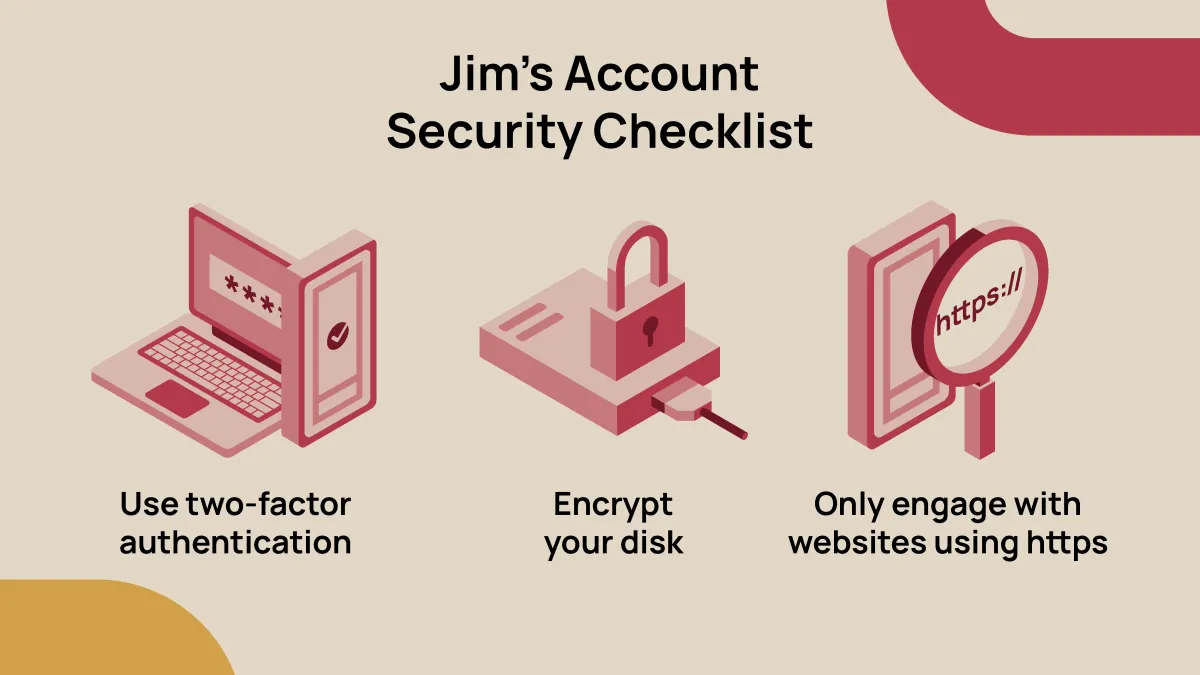
Security really depends on who your adversary is. Doing the simple things listed above will keep you safe from the rest of your family and co-workers, the kid down the block, and a majority of recreational hackers. If you know you are a target of more sophisticated hackers (you are a journalist doing investigative work, or a non-profit investigating human rights violations) then you need a higher level of security; organizations like the Electronic Frontier Foundation have checklists that will tell you what VPNs are best and the like.
If you are worried about the most sophisticated of attackers (say, the NSA or the Mossad) then you are in a very different universe and have to worry about everything from the physical security of your devices to how to do your work inside a network-proof area. But if these are the folks who are after you, what are you doing?
Interested in learning more about trending topics in data privacy from Mike and Jim? Take a look at some of their other blog posts below , or apply to join the next cohort of their course Data Privacy and Technology.
Related ArticlesJim and Mike on the Potential and Limitations of ChatGPT Image
Keeping Your Data Secure Image

|